Threat Modeling with OWASP Threat Dragon
Table of Contents
Table of Contents
Introduction
A threat model is essentially a structured representation of all the information that affects the security of an application. In essence, it is a view of the application and its environment through security glasses. - OWASP Threat Modeling
One of the problems we have in security is that often the people who are building the applications, the services, the systems, are not as familiar with what an attacker might do to try to break in. They may not have the attacker’s mindset. This situation is perfectly reasonable because most of the effort we spend is on just trying to get things to work, adding features, doing maintenance, etc. We often just don’t have the time to think about the attacker and what they might do to our precious systems and applications. Without that mindset, it can be difficult to create a threat model that is both complete and accurate.
At a high level, threat modelling is about asking questions. The following is from the threat modelling manifesto:
- What are we working on?
- What can go wrong?
- What are we going to do about it?
- Have we done a good enough job?
Threat modelling is a systematic approach to analysing system representations to identify security and privacy concerns. This process allows teams to identify potential problems early and throughout the lifecycle of a system, generating ‘threats’ that inform decisions in the design, development, testing and post-deployment phases.
One of the ways we can model threats is by creating a diagram, and that’s where Threat Dragon comes in.
Threat Dragon
OWASP Threat Dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle. Threat Dragon follows the values and principles of the threat modeling manifesto. It can be used to record possible threats and decide on their mitigations, as well as giving a visual indication of the threat model components and threat surfaces. Threat Dragon runs either as a web application or as a desktop application. - OWASP Threat Dragon
The Threat Dragon tool is available online, as well as a desktop application and a Docker image. There is also a GitHub repository for the project.
I’m going to use the docker image to run the tool locally.
docker pull threatdragon/owasp-threat-dragon:stable
Now I’m going to create a directory and set up some fake environment variables.
$ mkdir threat-dragon
$ cd threat-dragon
$ cat << 'EOF' > .env
ENCRYPTION_KEYS='[{"isPrimary": true, "id": 0, "value": "11223344556677889900aabbccddeeff"}]'
ENCRYPTION_JWT_SIGNING_KEY=asdfasdfasdf
ENCRYPTION_JWT_REFRESH_SIGNING_KEY=fljasdlfkjadf
NODE_ENV=development
SERVER_API_PROTOCOL=http
EOF
Now we can run the container.
docker run -it --rm -p 8080:3000 -v $(pwd)/.env:/app/.env threatdragon/owasp-threat-dragon:stable
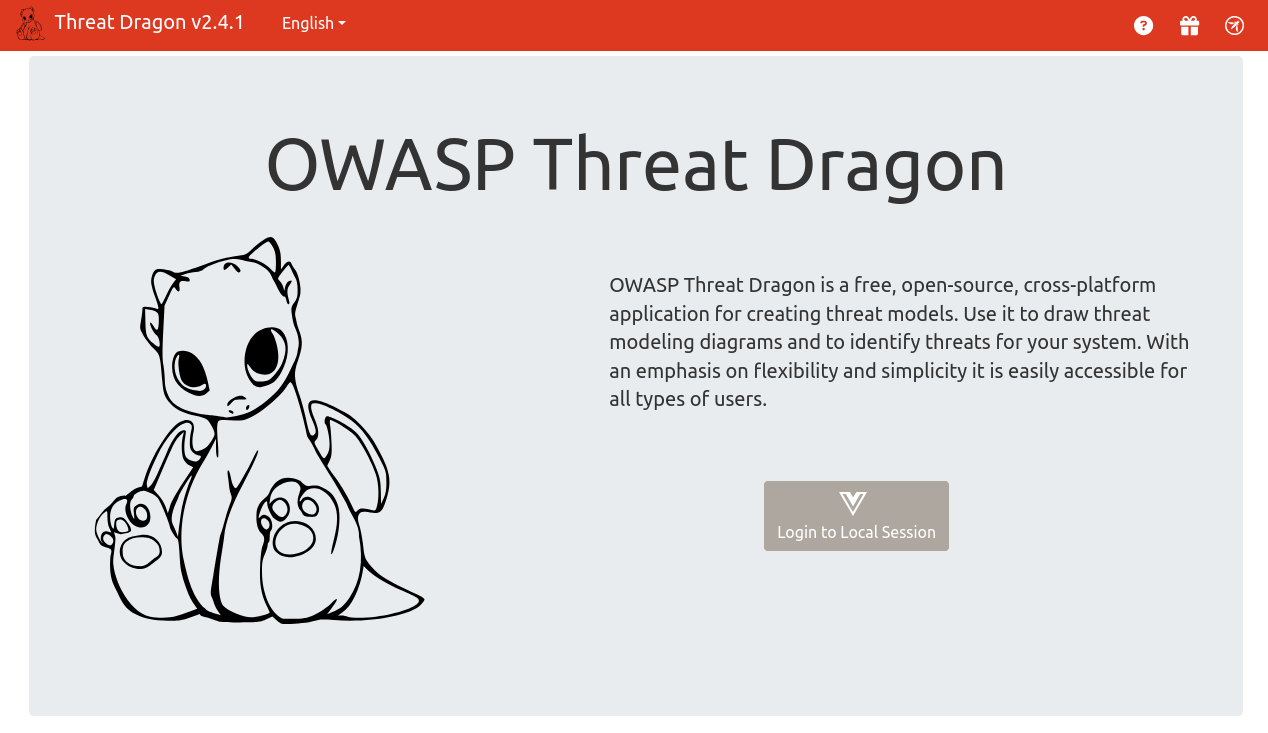
And if we go to localhost:8080 we can see the Threat Dragon application.
If we now click on ‘Log on to Local Session’ we can see some options.
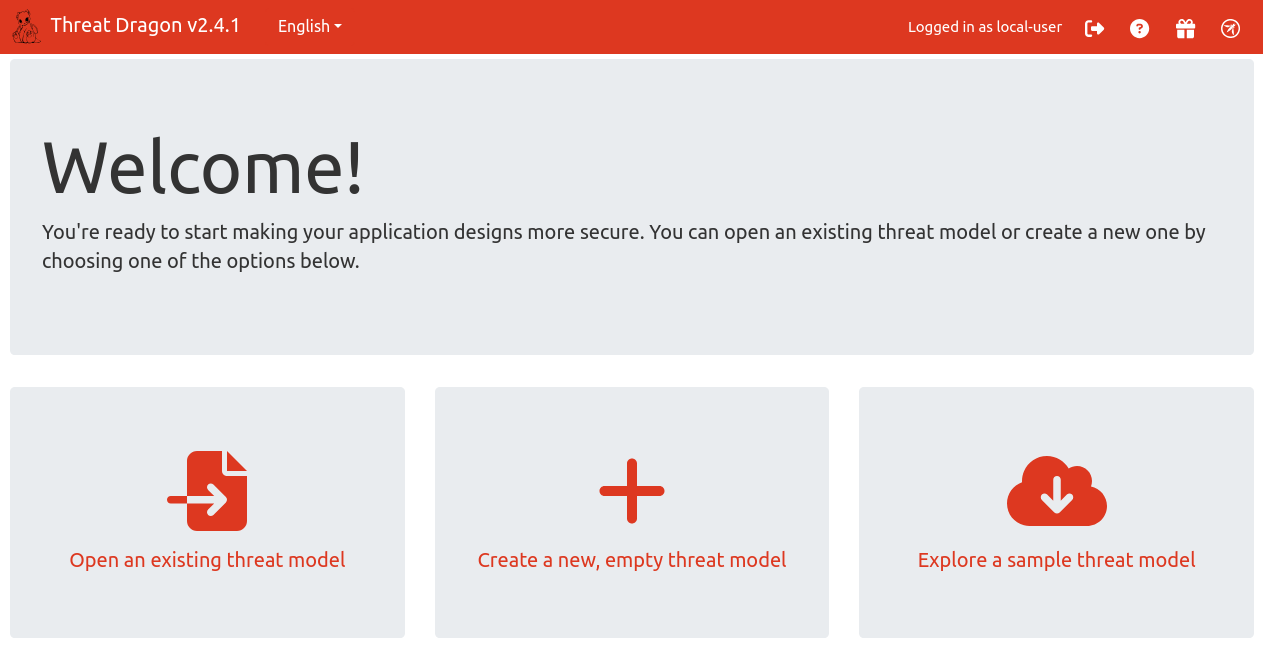
Next we select ‘Create a new empty threat model’.
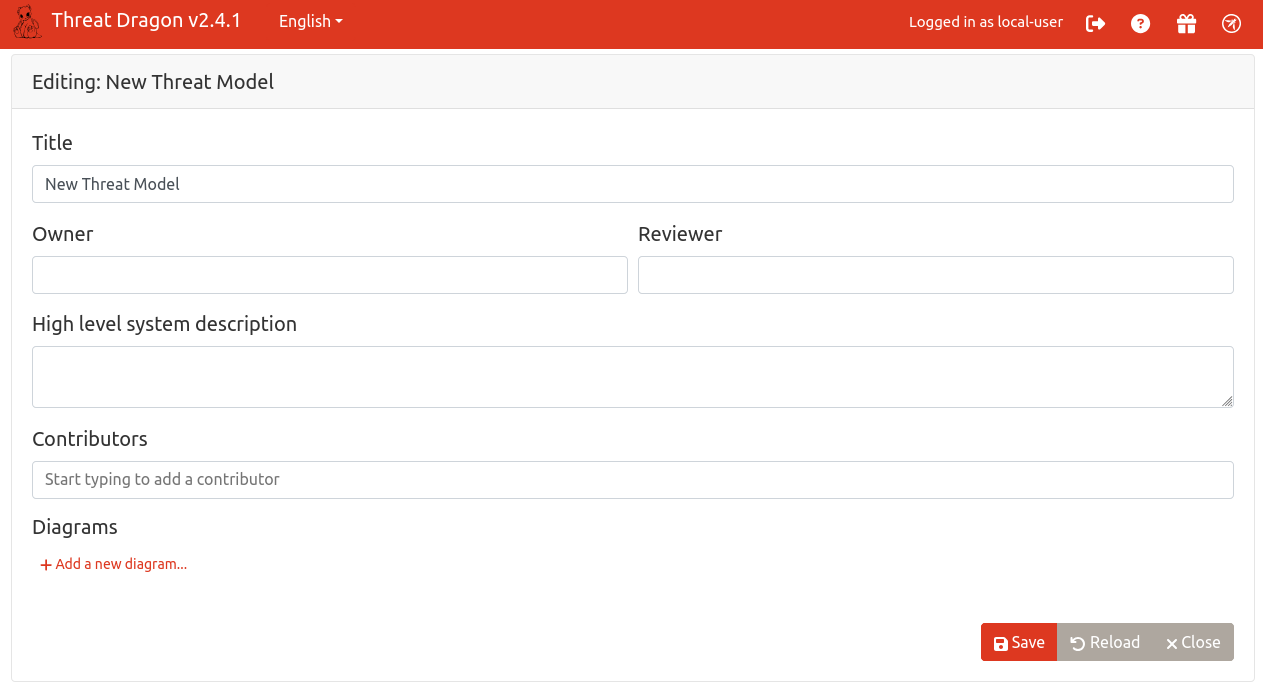
Now we can see the empty threat model and we can choose to create a new diagram.
Make sure you fill in all the required fields.
Now we can download the new threat model JSON file.
Once downloaded, go back to the main page and select ‘Import Threat Model’ and import the JSON file.
We should see the threat model on the main page.
Click on the diagram to begin editing.
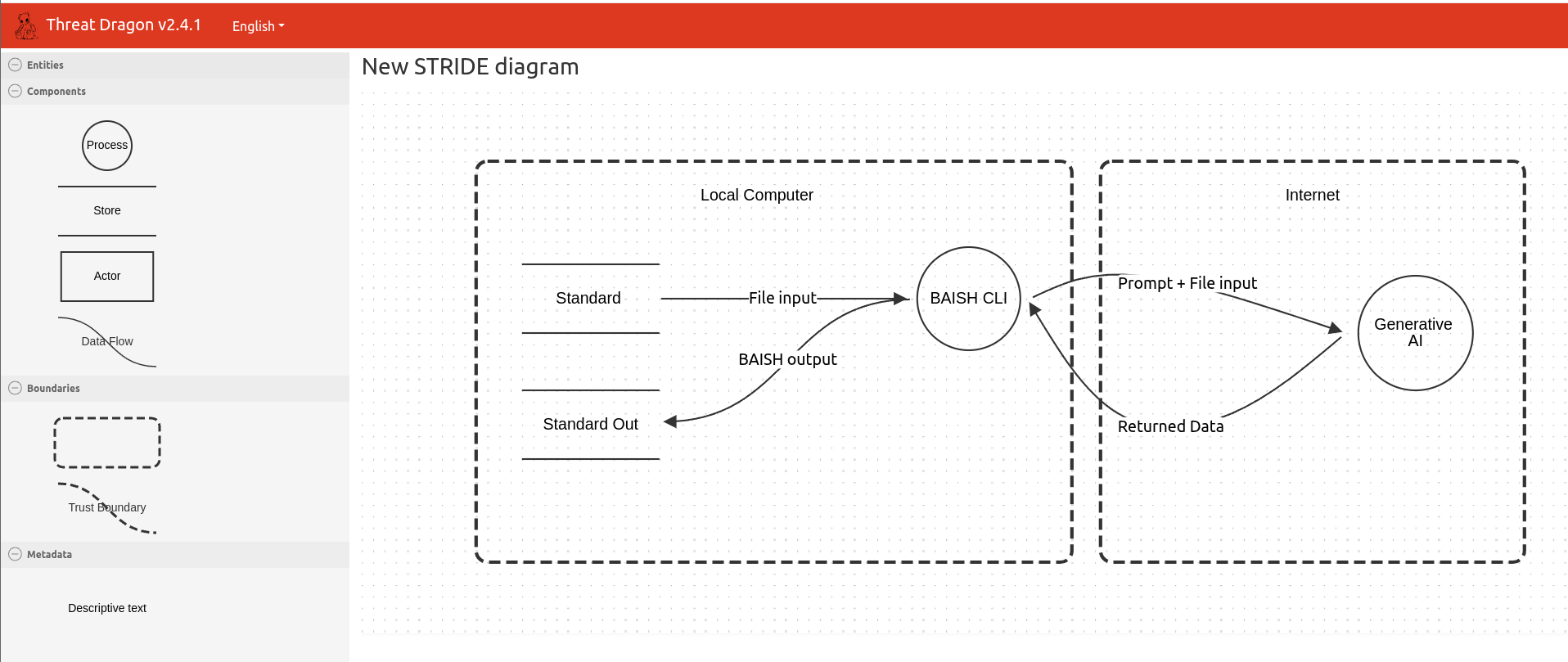
At this point we can start to build our diagram. Here I’m starting a diagram for our BAISH project.
Value of Threat Dragon
Ultimately, you could create a threat model diagram in almost any tool. I mean, I’m a big fan of Canva for making any kind of image or diagram, so you could use that. Or Mermaid diagrams might be better as they are code-based. One value of Threat Dragon is the ability to export the diagram as JSON, which you can manage in a version control system. You can’t do that with some generic diagramming tools. Mermaid, yes. Canva, no.
Also, Threat Dragon has some unique diagram shapes and components that give it a different feel. With fewer shapes, you aren’t overwhelmed with choices like you might be with some other diagramming tools. There’s just a few key shapes and lines that you can use to create a diagram.
That said, in the short time I’ve used it, I’ve found it a bit difficult to use. I need more time with it, but certainly other tools are easier to use, at least in the beginning. Dragging lines, deleting, moving things around–it’s fairly challenging to do in Threat Dragon.
Last point–this is an open source project, built by a handful of volunteers so of course they can’t make it like the “Canva” of threat modeling diagramming tools. There’s just not enough time, but what they have created is a solid foundation that you can build on, it’s certainly what you need to build a threat model diagram.
Next Steps
In future posts, we’ll take a look at exactly how to build out these diagrams and what all the different parts mean.


